February 1, 2026
Cybersecurity manifatturiera: NIS2 e Cybersecurity Act 2
Two out of five companies invest in security: MECSPE data and new EU rules simplifying compliance
Cybersecurity is no longer an exclusively IT issue, but a structural condition for the competitiveness of Italian manufacturing. This is confirmed by the MECSPE Observatory, conducted by Nomisma on 350 manufacturing companies: two out of five companies have already implemented IT security solutions or will introduce them within two years, positioning it in first place among the sector’s transformative innovations. At the same time, on January 20, 2026, the European Commission presented the Cybersecurity Act 2 and targeted amendments to the NIS2 Directive, to rationalize a regulatory framework that has become fragmented and burdensome, especially for SMEs. For B2B manufacturing companies, this convergence between national digital transformation and European governance represents a concrete opportunity: integrating security and innovation to scale in an increasingly interconnected market.
Manufacturing data: security as a prerequisite for AI and automation
The MECSPE survey (CAWI method, October-November 2025) reveals that cybersecurity is indicated by companies as a technological priority alongside artificial intelligence and energy efficiency, in a context where automation and robotics lead investments (47%) followed by process digitalization (41%). The cross-sectoral nature is evident: in high-tech sectors such as electronics, mechatronics, ferrous metals and additive manufacturing, cybersecurity is systematically among the three strategic priorities. Almost 30% of companies consider it an essential digital skill to develop over the two-year period, on par with robotics and Big Data. Maruska Sabato, Project Manager at MECSPE, summarizes: “The more companies invest in digitalization, automation and data use, the more fundamental it becomes to guarantee security, reliability and continuity of systems”. Angelo Giuliana from the Meditech Competence Center adds that “without solid security, AI doesn’t scale: companies hesitate to share data, integrate artificial intelligence into core processes and open up to digital supply chains”.
In practice, a mechatronics manufacturer implementing AI-based predictive maintenance must protect operational data from manipulation: only in this way does innovation become scalable and reliable. In a context of growing ransomware attacks and AI-powered offensives, cyber resilience becomes a prerequisite for maintaining contracts with global OEMs and complex supply chains.
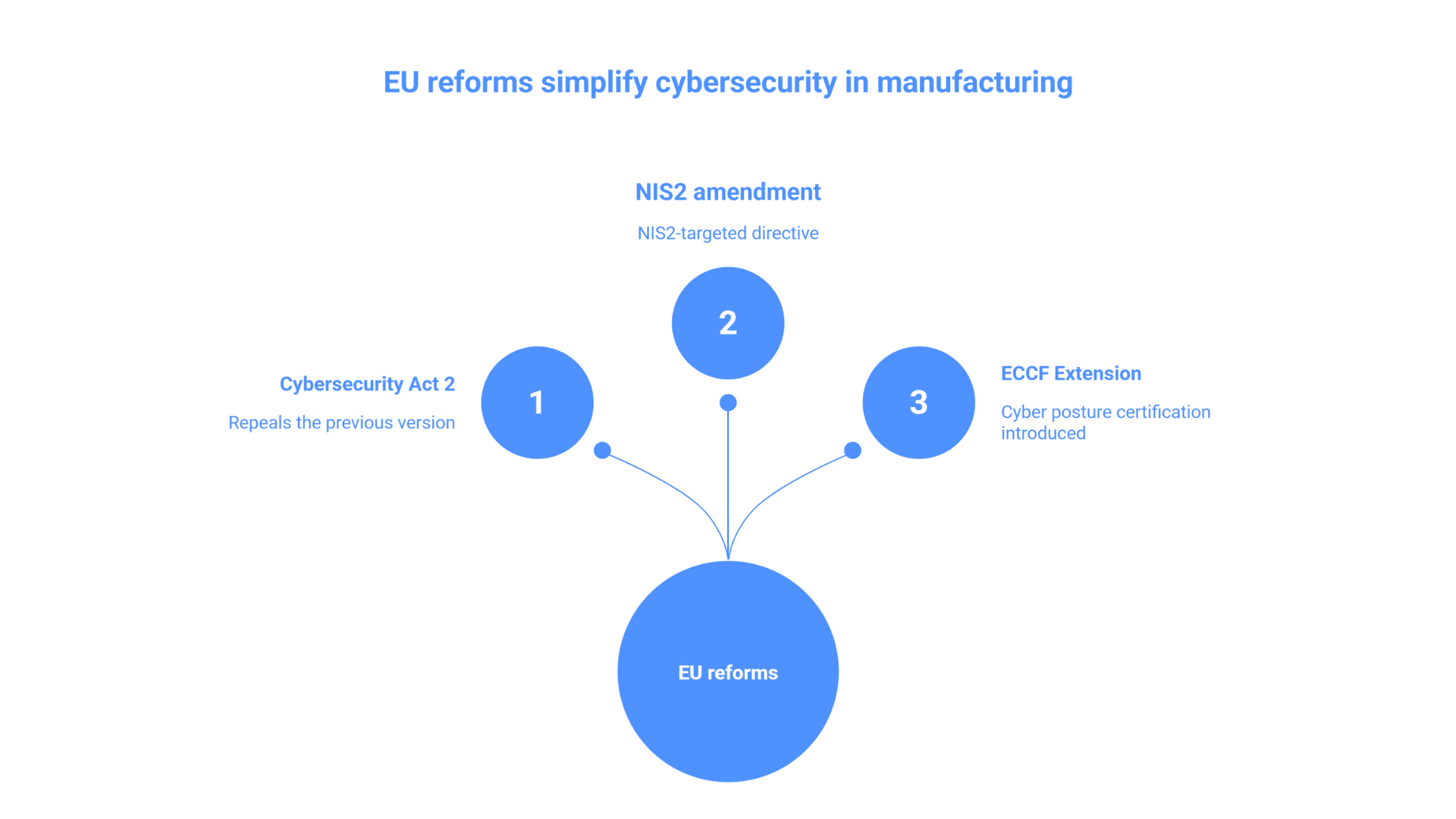
Cybersecurity Act 2 and NIS2: European simplification and accountability
In line with this growing need in European manufacturing, the EU Commission has initiated a rationalization of the regulatory framework on cybersecurity. Companies find themselves having to simultaneously manage ICT security requirements, data protection, operational resilience and continuity of essential services. The regulatory framework has in fact stratified rapidly in recent years. The European regulatory perimeter on digital security consists of a series of acts aimed at specific areas:
-
DORA (Digital Operational Resilience Act): regulation that imposes ICT risk management, resilience testing and incident management for the financial sector and its critical technology suppliers.
-
Cyber Resilience Act (CRA): establishes mandatory cybersecurity requirements for all digital products placed on the EU market, from design to decommissioning.
-
CER Directive (Critical Entity Resilience): requires critical entities to assess hybrid cyber-physical risks and implement organizational measures to ensure operational continuity.
-
Cyber Solidarity Act: for coordinated EU response to large-scale cyber incidents.
-
NIS2 (Network and Information Systems Directive 2): unified legal framework for the cybersecurity of networks and essential services in 18 critical sectors, with obligations for risk management, incident notification and supply chain security.
The EU reform package of January 2026 arises precisely from the observation that this proliferation of regulations has generated complexity that is difficult to manage, especially for small and medium-sized enterprises. The initiative proposes a new Regulation, called Cybersecurity Act 2, which repeals the previous version (Regulation (EU) 2019/881) introducing a more mature and coherent framework, accompanied by a directive with targeted amendments to NIS2. The objective is to harmonize procedures and requirements among Member States, reducing overlaps, national divergences and interpretative uncertainties.
Among the main innovations is the extension of the European Cybersecurity Certification Framework (ECCF), which introduces schemes on the “cyber posture” of organizations: regulated entities will be able to obtain certificates of compliance with risk management requirements, reducing compliance costs and supervisory burdens. The framework provides three levels of assurance proportionate to risk: basic (documentary review), substantial (testing on known vulnerabilities) and high (simulations of sophisticated attacks). This allows companies to calibrate investments and controls based on the criticality of their assets.
SMEs at the center: fewer burdens, more predictability
To further lighten the burden on small and medium-sized enterprises, the introduction into the NIS2 Directive of a new category of “small mid-cap enterprises” is planned, which designates them as “important” rather than “essential” entities. In this way, the supervisory burdens to which they must adhere are proportionally reduced: SMEs will be subject to reactive supervision (activated by incidents or reports) rather than routine proactive inspections, while maintaining the same technical standards for risk management as large corporations. This distinction recognizes that manufacturing SMEs, while playing a relevant role in production chains, operate with limited resources and require calibrated measures that balance security and operational efficiency.
Furthermore, when the Commission adopts implementing acts on NIS2 technical measures, Member States will not be able to impose additional requirements, ensuring uniformity and predictability. This means that an Italian manufacturing company also operating in Germany or France will be able to apply the same risk management procedures without having to adapt processes to divergent national specificities.
Supply chain and strategic sovereignty
The management of the ICT supply chain becomes a central element of the reform. Cybersecurity Act 2 introduces a harmonized framework to govern non-technical risks related to the supply chain: the Commission acquires the power to designate third countries at high structural risk, requiring companies to progressively phase out their components from critical assets (5G/4G networks, core network, virtualization systems) within a maximum period of 36 months from the publication of official lists.
This accountability logic also extends to conformity assessment bodies: conformity assessment bodies must guarantee full independence and are excluded from certification if classified as high-risk suppliers. Manufacturers and suppliers, through EU declarations of conformity, assume direct responsibility for the entire production chain, placing cyber security at the center of procurement strategies.
Operational NIS2: concrete obligations for manufacturing
The NIS2 Directive (2022/2555), already transposed in Italy with Legislative Decree 138/2024, extends the scope of cybersecurity to 18 critical sectors, including manufacturing. Since January 2026, an articulated notification system has been operational: pre-alert within 24 hours of detecting a significant incident to the National Cybersecurity Agency (ACN), followed by a detailed report within 72 hours and a final report within one month.
The sanctioning apparatus is proportionate to criticality: essential entities risk up to 10 million euros or 2% of annual global turnover; important entities up to 7 million euros or 1.4% of turnover. Manufacturing companies with more than 50 employees or 10 million euros in revenue – or considered critical regardless of size – must implement systematic analyses of vulnerabilities, operational continuity plans and structured cooperation protocols with competent authorities. For B2B players, NIS2 means extending controls and verifications along the entire digital supply chain: a requirement that is no longer optional for those competing in European markets.
Three concrete actions for manufacturing companies
To translate the regulatory framework into competitive advantage, three operational directions prove to be priorities.
1. Assess your cyber posture
Perform a structured gap analysis against NIS2 requirements and ECCF schemes, mapping critical assets, operational vulnerabilities and current protection levels. Identify which certification level – basic for standard processes, substantial for supply chain components, high for strategic assets – is appropriate for your risk posture.
2. Map and qualify the ICT supply chain
Systematically survey suppliers of digital components, verify their geographical origin and compliance with European standards, plan the phasing out of any high-risk suppliers within the 36 months provided by the regulations. This applies in particular to solutions that integrate OT/IT environments, IoT sensors and industrial control systems, where dependence on third parties can represent a critical risk. (For an in-depth technical analysis of IT/OT convergence and Zero Trust architectures in manufacturing, read our article: Cybersecurity and resilience: how it changes with IT, OT and AI)
3. Invest in internal skills
Train cross-functional groups on threat detection, incident response and proactive cyber risk management through practical exercises and simulations. The MECSPE Observatory places cybersecurity among training priorities for 30% of manufacturing companies: internal skills are the enabling factor for technologies that, without human governance, remain ineffective.
Cybersecurity as a differentiation lever
Italian companies are maturing awareness of the strategic value of cybersecurity to enable digitalization and artificial intelligence, while Europe provides clearer and more coherent regulatory tools. The alignment between industrial maturity and European governance opens concrete opportunities for B2B manufacturing operators. ECCF certifications become passports to high-compliance markets; strengthened accountability along the supply chain increases trust with manufacturers and international partners; the reduction of operational risks protects strategic investments in automation and artificial intelligence. It is no longer about fulfilling obligations, but about transforming security into a differentiating element.
An automotive supplier that integrates cybersecurity into its IoT sensors and obtains substantial certification competes for contracts with large European manufacturers that require guarantees along the entire production chain. A plastics SME that adopts integrated protection for operational and IT environments prevents ransomware disruptions, ensuring continuity to just-in-time delivery supply chains and consolidating its role as a reliable partner.
European regulatory simplification and the growing awareness of Italian manufacturing open a strategic window for SMEs: transforming cybersecurity from a regulatory constraint to a competitive lever is now more accessible and necessary than ever.
Main sources:
-
MECSPE Observatory 2025 (Nomisma) https://mecspe.com/cybersecurity-da-tecnologia-a-leva-strategica-le-imprese-la-indicano-come-principale-innovazione-che-sta-trasformando-il-manifatturiero-senza-sicurezza-non-ce-competitivita-industriale/
-
European Commission, Cybersecurity Act 2 and NIS2 (January 2026) https://digital-strategy.ec.europa.eu/it/policies/nis2-directive
-
Agenda Digitale, “Cybersecurity Act 2 and NIS2 reform” https://www.agendadigitale.eu/sicurezza/cybersecurity-act-2-e-riforma-nis2-cosi-lue-cambia-la-compliance/

Marta Magnini
Digital Marketing & Communication Assistant at Aidia, graduated in Communication Sciences and passionate about performing arts.

At Aidia, we develop AI-based software solutions, NLP solutions, Big Data Analytics, and Data Science. Innovative solutions to optimize processes and streamline workflows. To learn more, contact us or send an email to info@aidia.it.



